
Bussin’ it Down
The Difference Between a Good & a Great Public Adjuster + Home Insurance Claims Chat
Marisa Sanfilippo • April 28, 2023

Jeepin’ it Real
Interview with RooferGirl Samanntha De Coteau: Will She Make a Move to Florida from Canada?
Marisa Sanfilippo • April 7, 2023

iink Company News
iink and Momnt Make Restoration Property (Home) Financing More Accessible for Contractors & Property Owners
Marisa Sanfilippo • February 22, 2023
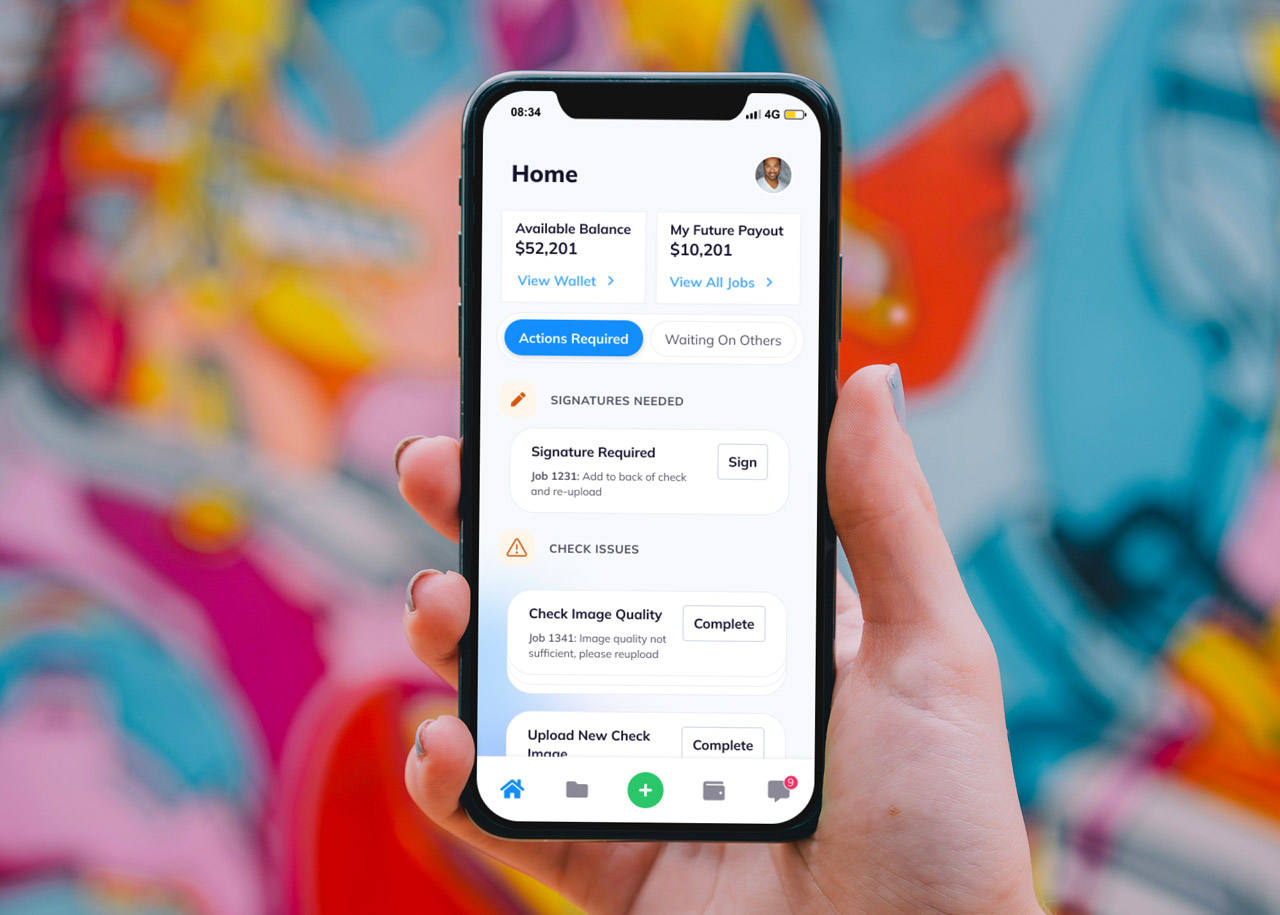
Payments Education
Insured’s Guide to Better Payments for Faster Restoration
Ryan Holliday • December 15, 2022

iink Company News
Payments Education
iink Product Information
Property Restoration Professionals: How Being iink Verified Gains You Trust From Customers & Prospects
Ryan Holliday • December 15, 2022

Payments Education
5 Tips for Success with Property Claim Checks
Ryan Holliday • December 15, 2022